Mining allows miners to get rewarded with a coin as compensation for validating blocks of transactions against consensus rules. Panda a Bilbao Spain-based cybersecurity company wrote in the beginning of February that a new malware variant has been taking over computers around the world hijacking them to mine.

Do You Have What It Takes To Mine Bitcoin Bitcoin Pro
The most popular method of distribution is via infected websites.

How does crypto mining malware work. One method works like classic malware. The script mines new cryptocurrencies on any. Woo is taking a close look at the flow of BTC to and from crypto exchanges.
Mining involves high computational and technical skills that miners need to have to bring the new coins to the market. Cryptojackers have more than one way to enslave your computer. 1 By verifying transactions miners are.
The industry of cryptocurrency mining has grown exponentially as more advanced hardware and software solutions are developed. This method uses malware specially designed for mining cryptocurrencies. Bitcoin mining malware detection isnt just about removing a nuisance from your device.
Basically cryptocurrency mining malware stealthily hijacks devices like computers or phones and steals their resources for mining cryptocurrencies. Cryptocurrency mining otherwise known as crypto mining is a popular topic on Internet forums. What does the crypto-jacking malware do.
Crypto Mining is a process of bringing any cryptocurrency into circulation for further investments and other reasons. Bitcoin mining has been a hot topic for the past years. You click on a malicious link in an email and it loads cryptomining code directly onto your computer.
Once activated such a malicious file can affect individuals as much as large enterprises that rely their operations on networks of countless servers. People fall prey by clicking a link in a phishing e-mail unintentionally loading crypto mining malware onto their computers. What is Cryptocurrency Mining Malware.
Loapi Monero-mining Android malware caused enough overheating to break devices. Be sure to watch out for the typical signs that youve got adware. In a nutshell this is crypto mining.
Mining is the process through which Bitcoin blockchain is secured and run allowing the decentralized network to function without the need for a single authority that verifies each transaction. There are three ways that crypto mining malware can become embedded on a victims computer. The cybercriminals use different ways to smuggle it onto the computers of their victims.
Crypto-mining malware in corporate networks. How does crypto mining work. The malware is named as BadLepricon the malware works on a highly sophisticated mining method wherein t picks up the wallpaper app to target its audience.
After successfully infecting a device the malware installs itself and uses the victims computers resources to mine Monero a cryptocurrency that offers greater anonymity than many of. They do this work by solving math problems like puzzle pieces which we call Proof-of-Work where they compete against each other around the world at the same time. The miner or mining pool who finds a block first gets the reward as long as their work is confirmed as valid across the rest of the network.
It is the work of the miners where they get crypto coins for their mining work. Once your computer is infected the cryptojacker starts working around the clock to mine cryptocurrency while staying hidden in the background. The work itself is done by miners whose computers perform millions of computations to change a given input into a required output.
New data on the amount of Bitcoin being scooped up by crypto whales How Does Cryptocurrency Mining Malware Work and retail traders signals the bottom is in according to on-chain analyst Will Woo. Lookout smartphone security company identified five separate apps that contained BadLepricon and Google removed the. How to detect and prevent crypto mining malware Hackers are placing crypto mining software on devices networks and websites at an alarming rate.
Cyber AI has discovered and thwarted hundreds of attacks where devices are infected with crypto-mining malware including. If it does the miner is rewarded with crypto. Here is everything you need to know about cryptocurrency mining and how it works.
Cybercriminals behind crypto mining viruses act with the purpose of profit. The first miner to produce the required output shares it with the network which then double-checks to see if its functioning and performing correctly. This convention is meant to keep Bitcoin users honest and was conceived by Bitcoins founder Satoshi Nakamoto.
Bitcoin Miner virus cryptocurrency mining malware or cryptojacking. This type of malware mines cryptocurrencies on your system using your resources in such a way you wouldnt know. Attackers inject a malicious code or script onto a website.
A server in charge of opening and closing a biometric door. How Cryptojacking Works. Exploiting the same security vulnerabilities as WannaCry Adylkuzz affected hundreds of thousands of computer earlier this year.
These tools can help spot it before it does. Covert cryptocurrency miners can present as adware as well. Adylkuzz is one of the largest pieces of cryptocurrency mining malware of 2017.
However not all are minable some of them are proof-of-work and others are proof-of-stake. Crypto mining using malware is a completely different matter. Its about improving the lifespan of that device.
This block of data then gets stored on the blockchain and a new block is ready to be solved. Cryptocurrency mining is the act of supporting and confirming transactions on a network in order to maintain it and validate transactions that are made by users of that network. What is Crypto Mining.
Whatever you call it it is the same form of cybercrime when fraudsters infect vulnerable computers with malware to steal computer processing power for illegal crypto mining. Cryptocurrency mining malware is typically a very stealthy malware that farms the resources on a system computers smartphones and other electronic devices connected to the internet to generate revenue for the cyber criminals controlling it. Crypto-mining malware has the ability to hamper and even crash an organizations digital environment if unstopped.
The malware was designed to attack and deliver via a wallpaper app. Crypto mining has only been around since Bitcoin first came to the fore in 2009 but since then it has made quite an impression with cybercriminals investors and minors. Right now there are thousands of different cryptocurrency coins.

Cyber Criminals Profit From Crypto Mining Malware Cpo Magazine Crypto Mining Malware Is Now The Weapon Of Choice For Hack Crypto Mining Say Google Cyber

Researcher Finds 50 000 Sites Infected With Cryptocurrency Mining Malware Cryptocurrency What Is Bitcoin Mining Bitcoin Mining

Bit Coins Bitcoinslogo Bitcoin Bitcoin Value Investing
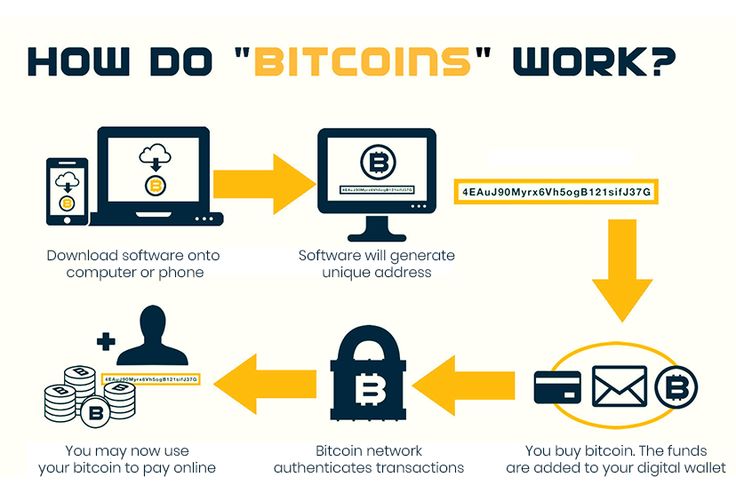
How Do Bitcoin Work Infographics Bitcoin Bitcoin Transaction Digital Wallet

Bitcoin Mining Hardware Evolution The Prevalent Hardware Were Insufficient To Meet The Coeval R Bitcoin Mining Bitcoin Mining Hardware What Is Bitcoin Mining

For A Long Time You Wish To Know About How To Know Your Bitcoin Wallet Address In Coins Ph But There S No Time The Free Bitcoin Mining Bitcoin Mining Bitcoin

Best Bitcoin Mining App Android Top 5 Btc Miner For Android Bitcoin Mining Bitcoin Mining Software Btc Miner

Firefox To Offer Users Automatic Protection Against Cryptocurrency Mining Malware Cryptocurrency Bitcoin Mining Software Cryptocurrency Trading

Cryptocurrency Mining Malware Targets Australians Via Sms Crypto News Cryptocurr Cryptocurrency Crypto Money Bitcoin Mining Software

This Cryptocurrency Botnet Was Designed To Seek And Destroy Mining Malware Seek And Destroy Cryptocurrency Ddos Attack

Risks Involved In Bitcoin Mining Btc Wonder

So You Want To Start Mining Bitcoin But Not Sure How To Start Or You Watched Bitcoin Mining Tutorials And Still Aren Bitcoin Bitcoin Mining Beginners Guide

How To Turn 0 1 Bitcoin Into 20 Bitcoins In 2 Months Make Money A Day Bitcoin Mining Bitcoin Investing In Cryptocurrency

Best Safe Bitcoin Cloud Mining Companies 2020 Bit Sites Cryptocurrency Investing Investing In Cryptocurrency

Everything You Need To Know About Bitcoin Mining Bitcoin Mining Hardware What Is Bitcoin Mining Bitcoin Miner

The Ultimate Cryptocurrency Cheat Sheet For Dummies Bitcoin Mining Bitcoin What Is Bitcoin Mining

Are You Just Getting Started With Bitcoin Mining We Have More Tips Here Https Howbitcoinworks Com Bitcoin Mini Bitcoin Mining What Is Bitcoin Mining Bitcoin

Here S Why Kaspersky Says Powerghost Is The Malware Of The Future Crypto Mining Malware Cryptocurrency


1 Comments
don't hesitate to place an order for a program card that can withdraw any amount you want. programmed cloned Cards are very transparent and easy to deal with. You can Purchase these cards and withdraw up to $50,000 to $100,000 limit without being detected because of the programming of the card. I'm extremely grateful to them for being honest with their words and delivering the card to me. This is the third day of receiving the card and I have withdrawn $9,500 from the Deserve Programmed Card. I tried purchasing the card previously from someone else, but it never arrived until I tried skylink technology for those in need of more money, you can also contact them. you can place order for the card Via whatsapp +1(213)785-1553 or their Email: skylinktechnes@yahoo.com
ReplyDelete